Leading Lever’s RBAC redesign to unlock $1.2M in retention
I led a 6-month overhaul of Lever’s Role-Based Access Control (RBAC) system, addressing a high-priority need from 32 customers representing $2.4M in ACV, and delivered a scalable solution that unlocked $1.2M in revenue retention, achieved 75% customer adoption, and drove a 57% lift in retention across previously at-risk accounts.

Context
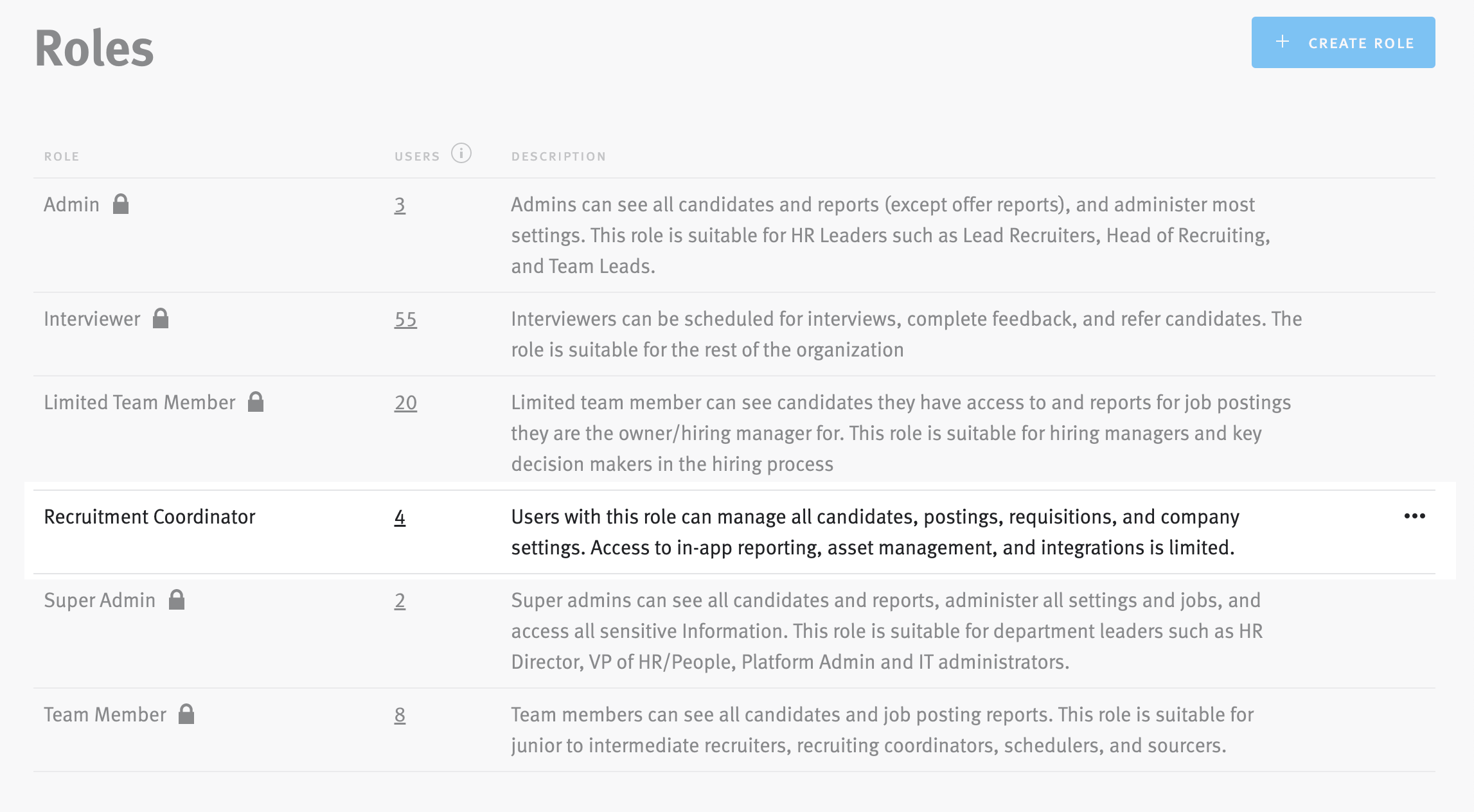
Lever is an Applicant Tracking System (ATS) that helps companies manage recruitment workflows — sourcing, interviewing, hiring. As customers scaled, their permission needs became dramatically more complex, but Lever’s system offered only five fixed roles with no flexibility. As a result, many Power Users simply gave Super Admin access to avoid roadblocks — exposing sensitive data, creating trust issues, and overloading support.
Over time, support teams were flooded with permission-related tickets, and 32 enterprise customers (representing ~$2.4M in annual contract value) flagged permissions complexity as a blocker to renewal or expansion. Internally, teams across Product, CS, Security, and Sales had conflicting mental models of what a “role” meant, causing friction in roadmapping and scope.
Opportunity
Rebuild permissions as a product experience, not just a technical safeguard. The goal: let admins create, adjust, and audit roles flexibly — without support or engineering help — while preserving security and clarity. The new system should reduce support burden, build trust, and allow Lever to confidently compete in enterprise deals.
Goals
- Maintain self-serve simplicity for admins across all customer segments
- Replace a brittle, static role model with a flexible permissions framework
- Reduce over-permissioning and its associated risks
- Align internal stakeholders across Product, Sales, CS, and Security, each with their own definitions of risk and success
- Create alignment on company-wide persona definitions and how those map to real customer roles and behaviors within the Lever platform.
My role
As Lead / Staff Product Designer, I owned both strategy and execution. I led research, mental model mapping, permission audits, UI design, usability testing, and rollout. I facilitated workshops across CS, Security, Product, Sales, and Legal to align scope and vision. I also established patterns that would scale, designing for future HRIS sync, audit logs, and region-based access governance.
- Foundational Research: Conducted a permissions audit and customer interviews to understand task-role mismatches. Mapped real job titles to required permissions and workflows.
- Market and Technical Analysis: Analyzed how competitors like Greenhouse and Workday approached RBAC. Partnered with engineering to explore the technical debt tied to Lever’s existing roles and enforcement logic
- Strategic Alignment: Facilitated workshops with Sales, CS, Product, and Security to align on MVP scope and future roadmap. Focused the initial release on unblocking critical workflows, while setting a path for deeper enforcement layers.
- Design & Validation: Introduced a modular Custom Roles builder with permission previews and grouped access levels. Ran 3 rounds of usability testing with real admins, iterating on visibility, naming, and mental models.
- Systematization & Rollout: Designed reusable system patterns for access tables, grouped permissions, and admin workflows. Authored training for internal teams, documented edge cases, and contributed to the legacy role migration strategy.
The process
- Permission Audit & Customer Interviews: I audited existing permissions, support tickets, and admin workflows. Conducted interviews across 10+ customers to map 22 real job titles to tasks and pain points.
- Competitive & Technical Analysis: Compared RBAC models in platforms like Workday, Greenhouse; worked with engineering to understand technical debt and enforcement constraints.
- Workshops & Alignment: Ran cross-functional sessions to align on MVP scope, prioritize use cases, and define domain boundaries.
- Prototyping & Testing: Built a modular custom roles builder with permission previews, toggleable permissions, grouped access sets. Iterated through multiple rounds of usability tests with real admins.
- Systematization & Launch Planning: Developed reusable UI patterns (tables, toggles, previews), documented edge cases, and created training materials. Migrated legacy roles to the new model carefully.
The research process
Our first step was to understand not just what was broken, but why it mattered.
- Internal & External Interviews: We interviewed 10 customers and mapped 22 unique job titles to real-world tasks. This revealed the core misalignment: existing roles didn’t reflect how teams actually worked. Coordinators were being given admin access just to schedule interviews; hiring managers could see sensitive recruiter notes that should have been private. Across the board, admins told us variations of the same story:
- “I have no idea what this person can actually do with the access I’m giving them.”
- “We had to file a ticket just to make a small change for one department.”
- “It’s too risky to test or tweak permissions because I don’t want to break anything.”
- Cross-Functional Discovery: We also ran sessions with internal partners — support, CX, implementation specialists, and admins. Each team was spending outsized effort firefighting the same access issues, without shared definitions of roles or scope.
- Audits & Benchmarking: We audited internal documentation, support ticket trends, and Lever’s default access groups. In parallel, I ran a competitive analysis of platforms like Greenhouse, Workday, and Rippling. Competitors offered granular controls but often at the cost of usability — a tradeoff enterprise buyers tolerated, but one we saw as an opportunity to differentiate.
Key Insight: This wasn’t just a technical gap; it was a trust gap. Customers wanted control without becoming full-time system admins, and internal teams needed guardrails to stop escalation loops. Our opportunity was clear: build precision and clarity without increasing friction.
Solution
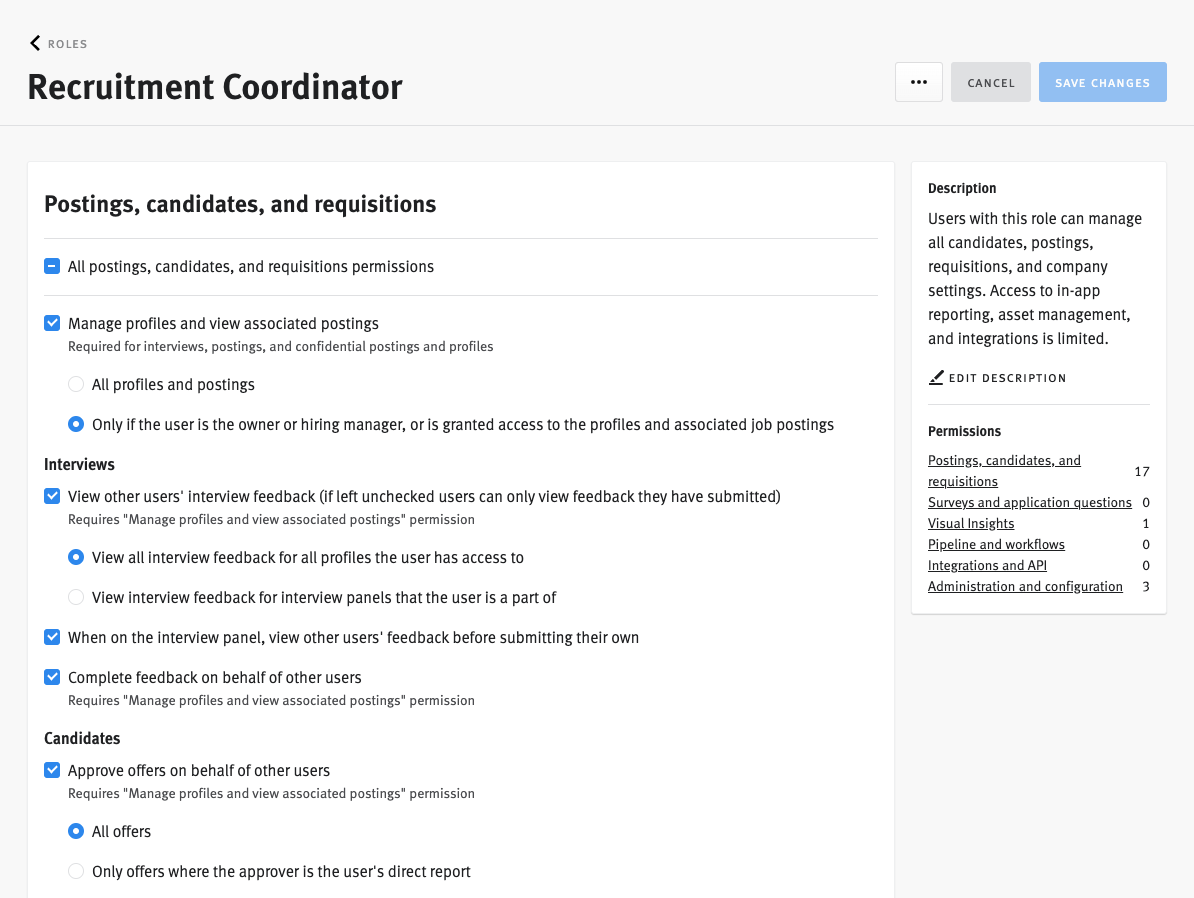
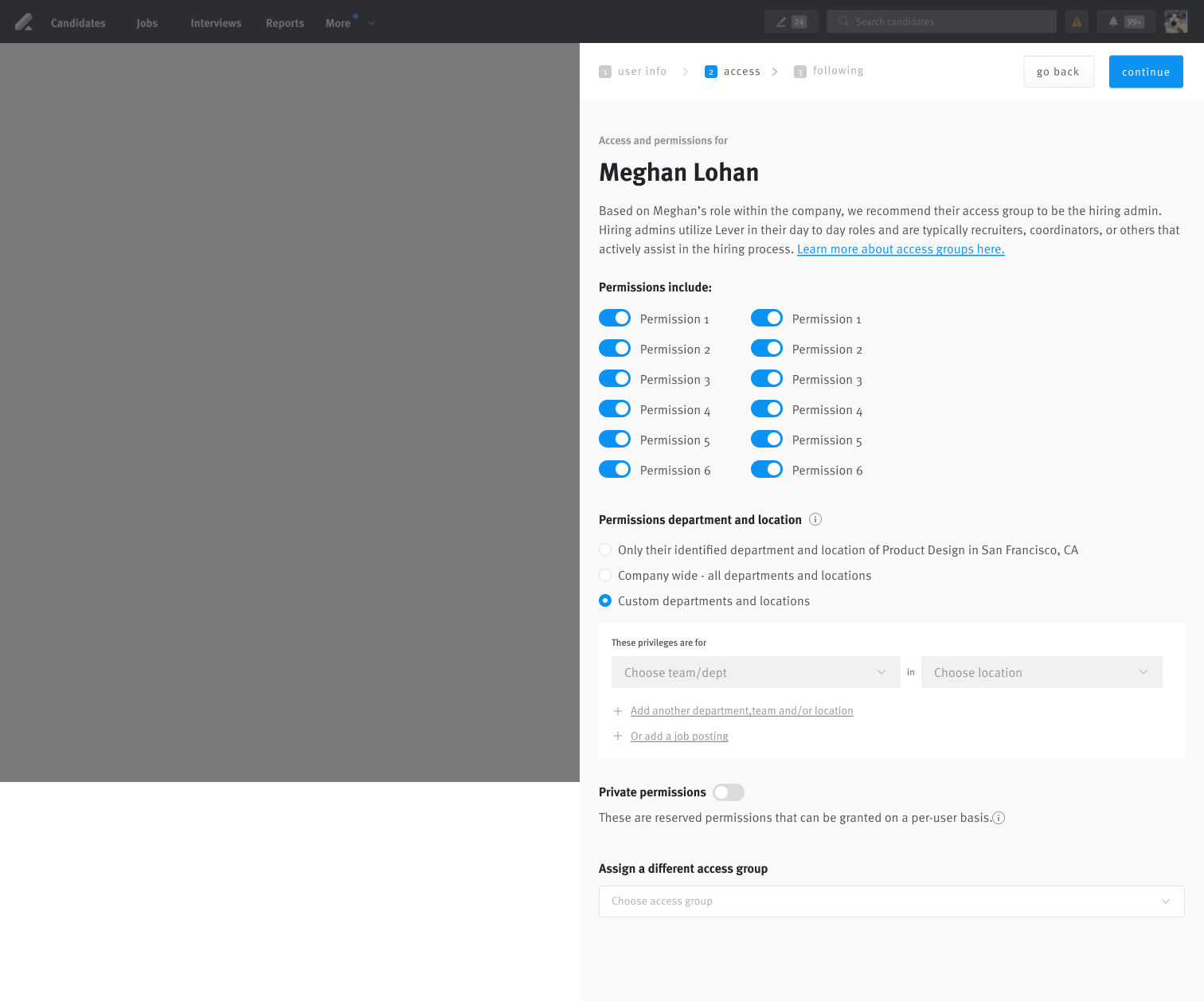
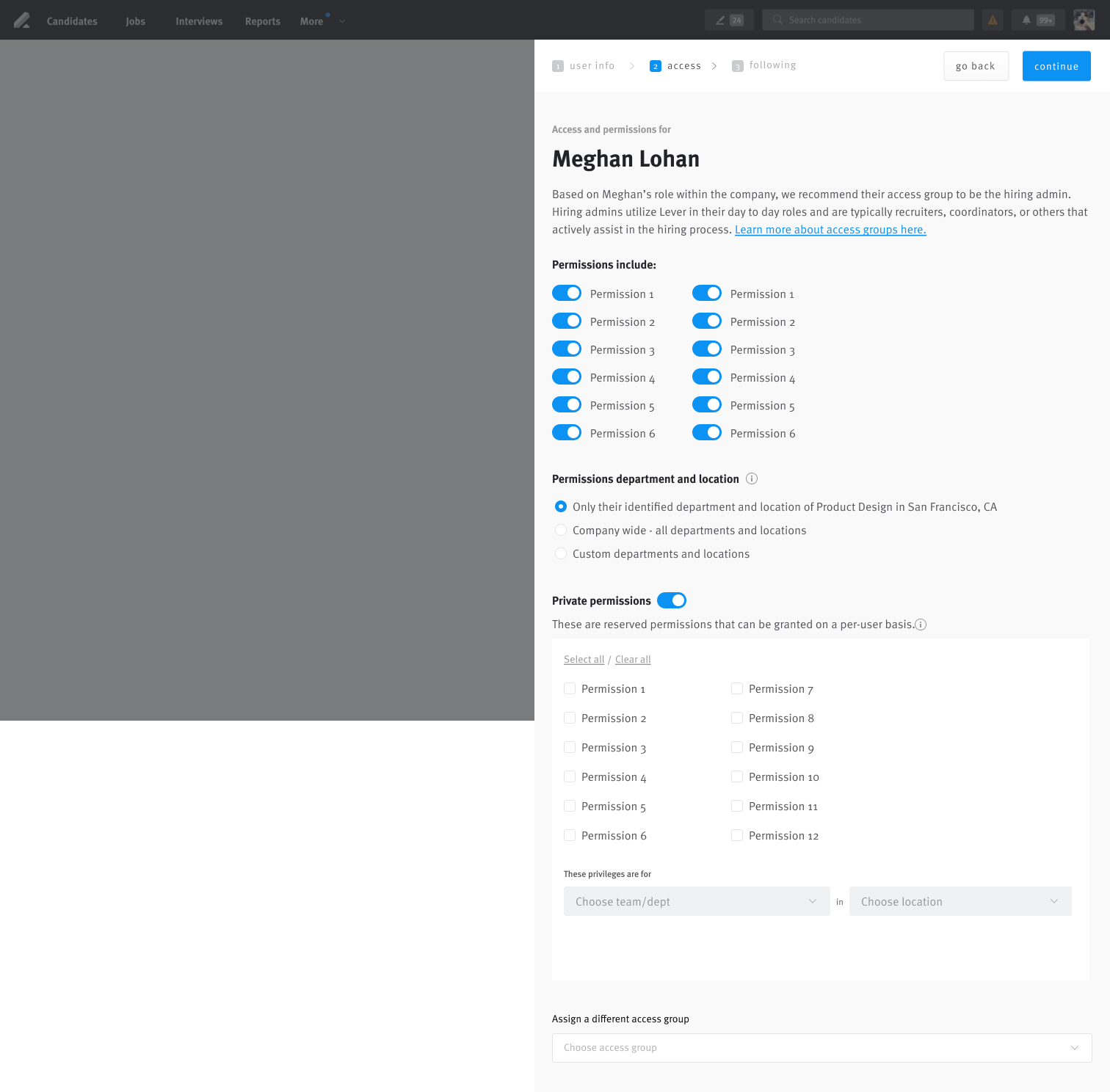
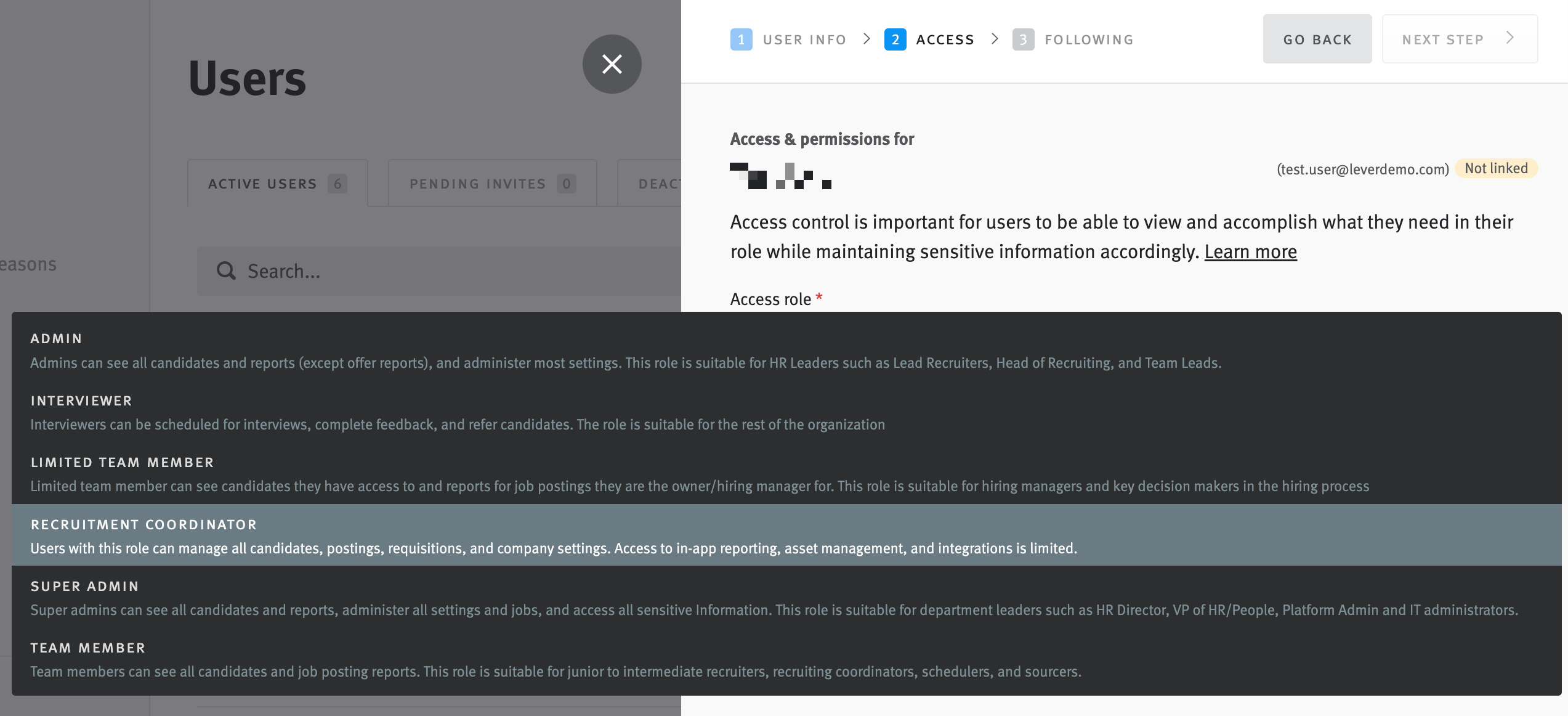
We delivered a self-serve permissions hub embedded in org settings. Admins could create custom roles (1–3) with fine-grained control, view all assignments at a glance, toggle permissions in context, and preview role impacts to reduce misconfiguration risk. The design balanced simplicity for small teams with configurability for enterprise scale.
Our MVP designs were guided by six principles:
- Reduce risk, make it scalable: Sync with HRIS tools like Workday or Rippling to ensure permissions track employee status, role, and org structure.
- Make users think less: Suggest permissions intelligently based on department or role, reducing guesswork.
- Make it easy: Provide just-in-time guidance and clear support paths to keep admins confident.
- Make it simple: Apply recommended sets automatically while allowing customization.
- Make it flexible: Allow granular tailoring for multi-team, multi-location orgs.
- Make it clear: Show exactly what each permission grants, replacing vague access titles with transparent, toggleable controls.
Admins can now:
- Create 1–3 custom roles from scratch with fine-grained control
- View a 360° dashboard of user access and role assignments
- Toggle permissions per-user in clear context (no guesswork)
- See previews of what a role enables, reducing fear of misconfiguration
The system retains simplicity for smaller teams, while giving enterprises configurability. Future plans included HRIS sync, audit logging, and region-based governance so the new system could scale with teams. As HRIS auto-provisioning rolled out, the hub transitioned from being the primary access control tool to an optional space for audits, exceptions, and visibility — still giving admins peace of mind, but reducing operational overhead.
Impact & outcomes
The launch of custom roles played a pivotal role in preserving $2.4M in contract value and contributed $1.2M in retention revenue by resolving a key blocker for large-scale customers. Within three quarters, the feature achieved a 75% adoption rate, validating its alignment with customer expectations around control and configurability.
- The redesign helped retain $1.2M in annual contracts by resolving permissions-related blockers.
- 75% adoption across enterprise accounts in the first few quarters.
- 57% lift in retention among previously at-risk customers after introducing custom roles.
- Shifted perception: Lever went from “not secure enough” to “enterprise-grade” in procurement and security reviews.
- Internally, teams across CS, Legal, Product, and Engineering gained a shared permissions framework, reducing cross-team ambiguity and enabling faster feature development and configuration.
Reflection
Permissions are a trust mechanism, not just a control panel. This foundation sets up audit logging, HRIS-based provisioning, and region-level governance. With HRIS as the source of truth, admins won’t need the hub for day-to-day org changes; it remains for audits, exceptions, and fine-grained adjustments.