Designing Lever’s Enterprise RBAC Framework: Driving $1.2M in Retention and Strengthening Acquisition Value

Summary
I led the redesign of Lever’s permissions system, introducing custom roles: a flexible, scalable RBAC framework that balanced simplicity for small teams with control for enterprises. This foundation preserved $2.4M in ARR, enabled $1.2M in retention revenue, and shifted Lever’s market perception from “not secure enough” to “enterprise-grade.”
Focus: Enterprise trust, security, and scale
Role & Scope
Title: Lead Product Designer, RBAC & Data compliance
Accountabilities: Research → Strategy → Execution
I led the full design lifecycle: permissions audit, customer interviews, competitive analysis, UI design, testing, and rollout. I also facilitated cross-functional workshops with CS, security, product, sales, and legal to align roadmap and governance. Design deliverables established patterns for HRIS sync, audit logs, and region-based access governance.
Design Challenge
Design a scalable, self-serve permissions experience that balanced simplicity for SMBs and configurability for enterprise teams, reducing support overhead and strengthening customer trust. Our primary persona for this set of work was the enterprise recruiting admin responsible for permissions for hundreds of users. Their job is compliance-critical: the wrong access means exposure of candidate PII, broken approvals, or failed audits.
Context
Lever is an Applicant Tracking System (ATS) that manages sourcing, interviewing, and hiring workflows. As enterprise customers scaled, their permission needs outgrew Lever’s static five-role model. Admins over-granted Super Admin access to bypass roadblocks, exposing sensitive data and overloading support.
Support teams were inundated with permission-related tickets, and 32 enterprise customers (~$2.4M ACV) flagged permissions complexity as a renewal blocker. Internally, Product, CS, Security, and Sales all held conflicting definitions of what a “role” meant, leading to fragmentation in scope and accountability.
Admins couldn’t answer two basic questions: Who has access to what? and Which role is appropriate? That uncertainty wasn’t a nuisance; for enterprise accounts, it was the difference between renewal and churn. Our customer message was clear: ‘Make this trustworthy and operable at scale, or we leave.
Cross-Functional Partners
- Engineering: technical feasibility & enforcement logic
- Security: compliance, risk thresholds
- Customer success: renewal insights & ticket triage
- Sales: deal blockers & procurement requirements
- Legal: privacy & data exposure policy alignment
Problem Details
Lever’s static role model limited flexibility and created organizational risk.Admins were over-permissioning to avoid friction, giving unintended data visibility across hiring teams. The permissions design was built for small teams, but our customers now had thousands of seats across regions and business units.
Reality: Only 5 rigid roles → access inflation → auditors unhappy.
The Impact
- High-risk Super Admin distribution
- Rising enterprise dissatisfaction
- $2.4M in ACV at risk from permissions friction
- Misaligned internal definitions of “role,” “access,” and “ownership”


Why It Mattered
Enterprise customers equate control with trust. By giving admins precise yet intuitive access management, Lever could increase retention, reduce support burden, and confidently compete in enterprise procurement cycles.
Goals
- Maintain self-serve simplicity while adding enterprise-grade flexibility
- Replace brittle fixed roles with a modular permissions framework
- Reduce over-permissioning and risk exposure
- Align Product, Sales, CS, and Security around shared definitions of “role”
- Create consistent persona mappings between internal definitions and real-world customer workflows
The Research Process
Permission Audit & Customer Interviews
Reviewed permissions data, support tickets, and admin workflows.Interviewed 10 enterprise customers and mapped 22 real job titles to tasks and pain points.
Takeaways
- Coordinators had admin access just to schedule interviews
- Hiring managers saw private recruiter notes
- Admins avoided testing changes out of fear of breaking access
“I have no idea what this person can actually do with the access I’m giving them.” and “It’s too risky to tweak permissions because I don’t want to break anything.”
Cross-Functional Discovery
I led cross-functional workshops with Product, CS, Sales, and Implementations to align on MVP scope, domain boundaries, and a shared risk language. We codified role definitions and permission groupings so support, sales, and product told the same story. This also produced the first consistently used persona set inside product.
Competitive & Technical Analysis
Benchmarked against Greenhouse, Workday, and ICIMs. Partnered with Engineering to identify technical debt and enforcement constraints.
Key Findings
This was a configuration issue and a trust problem. Customers wanted autonomy without complexity; internal teams needed guardrails and shared definitions.
- We collapsed persona noise into a durable mental model and set principles.
- We refined the 22 personas into four durable roles that consistently intersected with access decision
- We reduced ambiguity as a feature, not as a memo.
From there, I combined customer research with internal discovery to identify consistent failure modes:
- Access inflation (too much access by default)
- Orientation gaps (admins couldn’t see ‘who has what’),
- Management gaps (no framework for ‘appropriate access’),
- and provisioning gaps (no bulk/audit workflows).

Strategy
I structured the redesign into five connected workstreams:
- Audit & mapping: connected real-world roles to actual permission needs
- Competitive & technical benchmarking: evaluated feasibility and market parity
- Workshops & alignment: unified CS, Sales, and Security definitions under one model
- Prototyping & testing: built and tested modular Custom Roles builder with permission previews and grouped toggles
- Systematization & launch: created reusable patterns, documented edge cases, trained internal teams
Solution
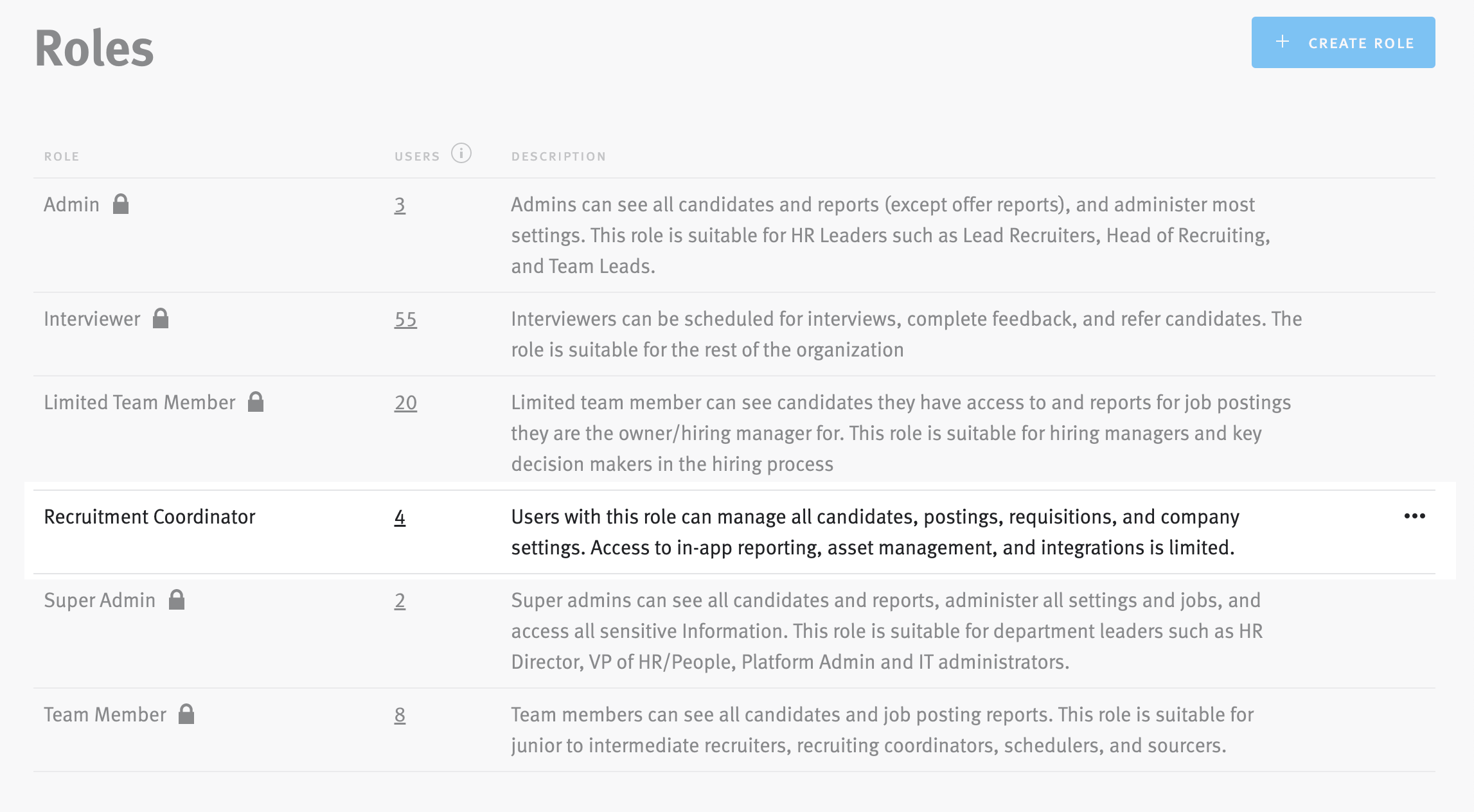
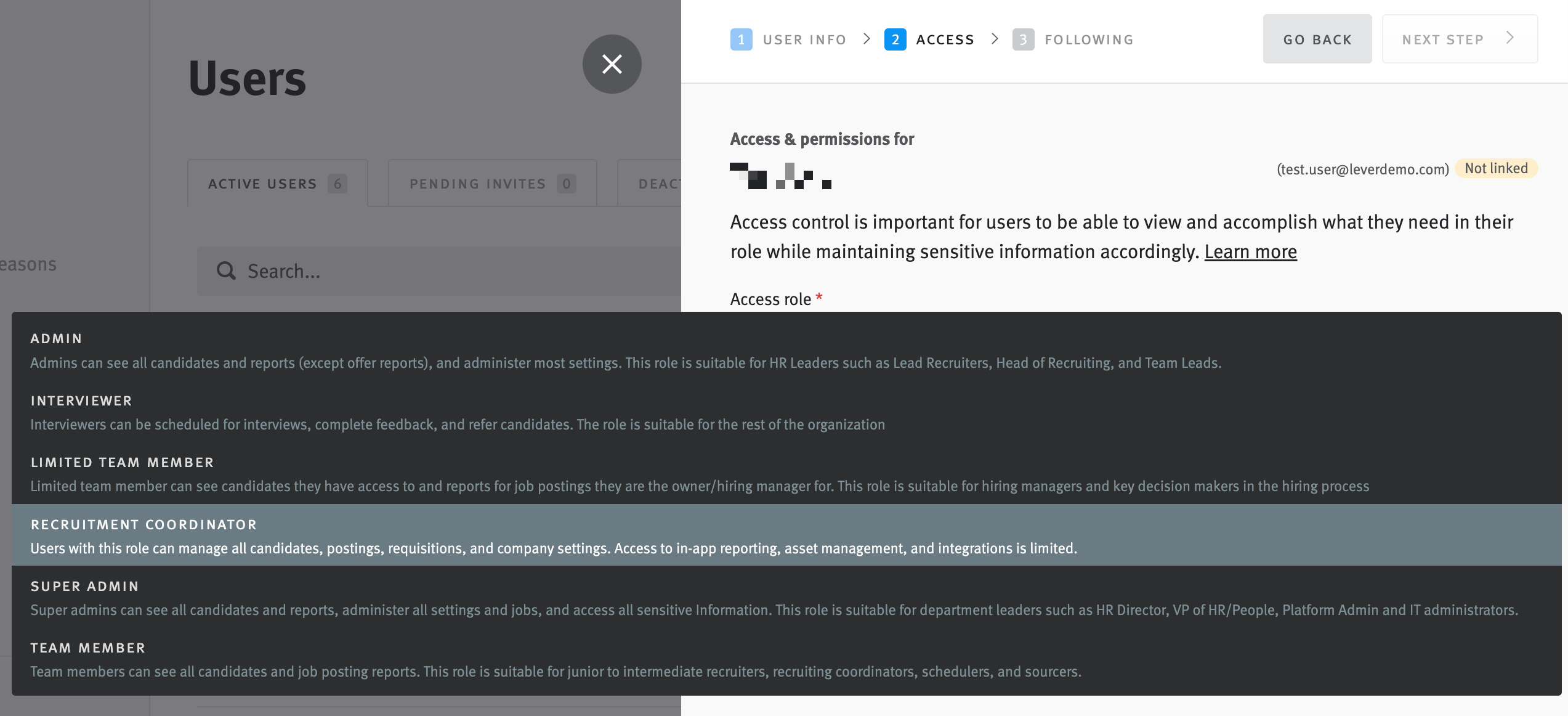
The MVP delivered a self-serve permissions hub embedded in org settings, combining enterprise-grade configurability with admin simplicity. Admins can now:
- Create 1–3 custom roles with fine-grained controls
- View all user access and assignments in one dashboard
- Toggle permissions contextually (no guesswork)
- Preview what each permission enables before applying
Design Principles
- Reduce risk, make it scalable: integrate HRIS sync with Workday or Rippling
- Make users think less: suggest permissions based on role/department
- Make it easy: inline help and contextual guidance
- Make it simple: recommended default sets with override options
- Make it flexible: multi-team, multi-region tailoring
- Make it clear: plain-language permission labels and grouped access
Custom Role Creation


Outcomes
- Preserved $2.4M in enterprise contract value
- Delivered $1.2M in retention revenue
- Achieved 75% adoption across enterprise accounts
- Drove 57% lift in retention among at-risk customers
- Shifted perception from “not secure enough” to “enterprise-grade”
- Reduced ambiguity across CS, Legal, Product, and Engineering
The new permissions framework elevated Lever’s enterprise credibility, reduced dependency on support, and created a scalable foundation for audit logging, HRIS provisioning, and region-based access governance.